A lot of hosting suppliers have to be through serious problems caused because of the distributed denial-of-service attack (DDoS attack), as DDoS attacks transfix their network. Before you read further there may be a nice example that explains DDoS Protection better: DDoS attack is far almost like a collection of individuals standing right before of a store and state of affairs the doorway. Crowding makes it tough for legitimate purchasers to enter, thus the trade is interrupted.
What will DoS and DDoS attack mean?
In a Denial of Service (DoS) attack Web Protocol address (IP address) is bombarded with the large quantity of traffic. If the targeted IP address points out at a selected server, then because of the bombardment entire server gets flooded. This ends up in service denial, and as services from the online server gets disabled. All the legal traffic is lost because the server becomes inaccessible.
Let’s perceive what DDoS attack. A DDoS attack is an attempt taken by an aggressor to disable online services for users, typically by suspending all services at the hosting suppliers finish. This attack is mostly a malicious one. A distributed denial of service attack (DDoS) may be a completely different and special kind of DoS attack. Its principle is analogous to the DoS attacks principle. The sole distinction is that bombardment of traffic towards the web server is generated from various sources and directed towards one end. Since there are various sources of traffic generation, usually from throughout the world. It makes the DDoS attack tough to block as compared to the one from only one IP address.
DDoS attacks and their frequency:
These days the DDoS attacks are increasing at an alarming rate. A giant reason is that the growing range of unprotected devices that are principally enabled by the Internet of Things (IoT) technology that is infected and incorporated into botnets. Also, it's been analyzed that there's a big rise within the DDoS attack victims because of the large volume of data. A contributor to any or all these attacks is that the Memcached attacks just like the Memcached amplification attack technique.
It is been surveyed that cybercriminals have fired over 15,000 Memcached attacks at the start of this year. One among them included an attack on GitHub that had a possible to attain concerning 1.35 TBps.
Another survey by Corero Network Security created an analysis that mentioned between quarter 2 and 3 of 2017, DDoS attacks have exaggerated by concerning 35 %.
It is necessary for enterprise owners to know however these attacks are harmful and additionally a way to stop them before it starts damaging business.
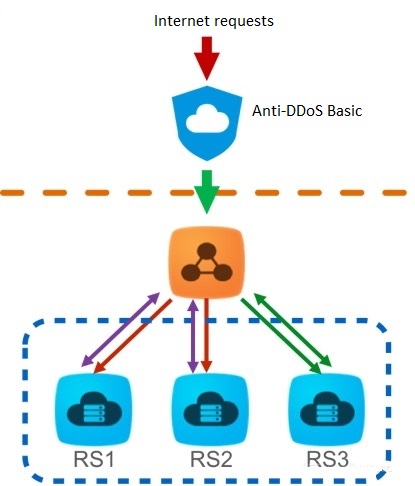
Here’s how Host provides solutions which will scale back damages by DDoS:
Host ensure all the websites and servers are secured against all the kinds of DDoS attacks given below address all of these with an exclusive set of tools and defense strategy:
Volume-based mostly Attacks: so as to face against multi-gigabyte DoS or DDoS attacks, Host ensures that all attacks are absorbed on demand by a network of scrubbing centers.
Protocol Attacks: The protocol relates to attacks are mitigated by blocking the ‘Bad’ traffic much before it reaches the online server and attacks it.
Application Layer Attacks: Application layer attacks are mitigated by Host by observing the behavior of guests. There are some preventive measures taken up majorly for mitigation of attacks resembling blocking unhealthy catboats and un-identifiable entities with the help of CAPTCHA, Cookie Challenge, and JS check.
These days it’s necessary for all online businesses to spot and realize DDoS mitigation so selecting and then choosing a suitable way to eliminate these attacks.
Final Note:
Just in case if you're getting to select a scrubbing center. Ensure you get an inline threat tool for mitigation deployed. The tool ought to be capable of recognizing and analyzing and should answer all inbound DDoS attacks. This may result in a giant modification in automatic DDoS mitigation.
One should select efficient and economical DDoS security services which have further potential to extend client’s safety and additionally guard hosting provider’s network, infra, and assets.

Hi Admin,
ReplyDeleteI have been just watching that blog, It is really Impressive. Just loved that information content of that blog. Keep writing the stuff like that. Thanks!!
New Zealand Dedicated Server
love the post !!!
ReplyDeleteThank you for your intelligent post and for helping others become more aware. You made more sense than others who speak within this same area of expertise and I am really glad I found your blog-website. I’ve joined your social networks and will keep an eye out for future great posts as well. Additionally, I have shared your site in my social networks as well. Thank you again!
Norton Phone Number Customer Service
Hi Admin,
ReplyDeleteI have been just watching that blog, It is really Impressive. Just loved that information content of that blog. Keep writing the stuff like that. Thanks!!
Norton Phone Number Tech Support